Societal Relevance of BGP
BGP and rerouting data
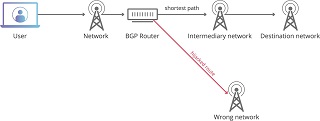
The Internet is highly dynamic: the distribution of IP addresses by ISPs is constantly changing. BGP ensures that these changes propagate from AS to AS. Unfortunately, BGP has no built-in verification methods, and as a consequence, malicious changes are also propagated. This means that an AS can announce IP ranges it does not own, resulting in the unwanted rerouting of data over the Internet. An example of this unwanted rerouting was caused by the government-controlled ISP Rostelecom in 2017:
Confidential networking traffic of MasterCard, Visa, and other large financial services was briefly rerouted through the Russian government-controlled ISP Rostelecom. Although unwanted rerouting of data caused by BGP-related misconfigurations can occur, the sudden rerouting of a dozen of IP ranges for important financial services is, to say the least, suspicious.
BGP comprises over 20 decision criteria that determine whether a new learned route, used to interconnect ASes and direct Internet traffic, will be accepted by an AS. Very few people understand BGP and are able to configure the hardware for it. Moreover, adding new IP ranges, for expanding connectivity, is a manual process which can easily cause misconfigurations leading to unintentional BGP hijacks. As a result of these unintentional BGP hijacks, the malicious actor performing the hijack can simply state that it was a misconfiguration. A few months after the Rostelecom hijack, another suspicious incident occurred where popular American IP ranges were hijacked. This was again picked up by the media in late 2017.
Traffic sent to and from Google, Facebook, Apple, and Microsoft was briefly rerouted through a previously unknown Russian AS, again under circumstances researchers say were suspicious and intentional. Between 40 and 80 separate IP ranges were affected in two hijacks and the AS responsible for the hijack, which received terabytes of data, was only active during the hijack.
BGP and spam
BGP is also misused for sending spam. In 2018, Bitcanal, a Portugees company, hijacked IP ranges and used it to send spam. With the help of the Internet community and publicly available BGP data, the large ISP Hurricane Electric and Portugal’s IPTelecom managed to disconnect Bitcanal from the Internet. Bitcanal hijacked a total of 130 IP ranges comprising over 240k IP addresses.
BGP and Internet censorship
The interdomain routing protocol is sometimes used for applying Internet censorship. Again, given the complexity of the protocol, and the way ISPs are interconnected, neighboring ASes can also experience unintentional negative effects. The way in which Pakistan knocked YouTube offline and how Iran imposed a ban on the messaging app Telegram serve as prime examples.
In February 2008 Pakistan’s state-owned ISP managed to cut YouTube off the Internet. The ISP, after receiving a censorship order from the telecommunications ministry, began announcing Youtube’s IP ranges to black hole all traffic destined for Youtube servers from Pakistan citizens. While they were meant to stay within country borders, BGP announcements reached ISPs in neighboring countries resulting in a world-wide outage of the Youtube website.
To tighten the state-imposed ban on the Telegram messaging app, an Iranian ISP temporarily rerouted Telegram app traffic in July 2018. For one hour, BGP traffic destined for Telegram was black holed rendering the app unusable. By altering the routing of Telegram traffic, the Iranian ISP also rendered the app useless for other users in neighbouring countries.
As the incidents above demonstrate, route leaks, the forwarding of BGP messages to ASes that are not supposed to receive them, are a great risk to the stability of the Internet. The largest route leak related incident occured in August 2017 where large parts of Japan could not reach the Internet for a couple of hours because of route leaks of over 135.000 IP ranges by Google. Consequently, the largest ISP of Japan used Google’s AS to reach other parts of the Internet. However, because Google is not an ISP, the AS could not handle all the traffic and caused the outage.
BGP and security
Back in the days when BGP was developed, not many ASes existed, and relationships between ASes were mostly built on trust. Consequently, BGP did not need authentication measures for announcing routing information. Nowadays, trust alone is not sufficient and the absence of proper security measures makes BGP more vulnerable to hijacking attacks. A security extension called BGPSec exists. BGPSec implements path validation and ensures that information about the path, taken by the BGP announcement, cannot be altered. Unfortunately, BGPSec is hardly implemented because new hardware is required. Also, the security extension only works if everyone in the path supports it.
The last 3 years there have been around 200-250 BGP-related incidents per month. There are two main reasons why these numbers do not drop:
For ISPs, there is a lack of awareness: the tendency of not sharing BGP traffic does not help to solve the hijacking problem. Of the 70k plus ASes that exist, only about 500 ASes share their BGP traffic with forums that are open to all parties with an interest in increasing visibility and stopping hijacks. As a consequence, the impact of hijacks is only partly visible. Moreover, configuring BGP is a challenging task, making it a specialty.
For an Internet user, BGP is not visible and the impact of hijacks is not always immediately clear. But, the consequences of a hijack can be severe as shown earlier: in the case of the Rostelecom hijacks in 2017, confidential data was compromised by a Russian ISP. When Internet users have no knowledge about the impact of hijacks, ISPs are less motivated to address this problem. This lack of visibility concerning BGP-related information gives malicious actors free rein. A hijack on an IP range far from its source, most likely will not be mitigated if detected. To increase awareness about the importance of sharing BGP-related information, there should be more insight into how hijacks are affecting Internet routing. Given that the currently available BGP routing data does not cover all regions, simulating the impact of hijacks can provide insight about where coverage is lacking and about who is affected. To be able to perform accurate simulations, the simulation database should resemble the Internet topology as much as possible.
Finally, around 20% of the hijacks last less than ten minutes, and some can pollute 90% of the Internet in less than two minutes [40]. This means that the real-time detection of BGP anomalies is required to be able to act accordingly. But, just detecting them is not enough: operators need to still mitigate the attack.